WhiteStar Secure Network Platform (SNP)
WhiteStar Secure Network Platform (SNP) is an AI-enabled overlay network operating system with advanced cryptography that does not require access control lists or public key infrastructure (PKI) certificate management. WhiteStar SNP works with systems on premises, in the cloud, as virtual machines, or physical systems owned by the customer. WhiteStar SNP delivers point to point networks that provide secure access to devices, services, and infrastructure without relying on centralized brokers.
Secure Architecture
WhiteStar SNP reduces a network’s attack surfaces, the places which a cyberthreat can exploit, to a maximum of one rather than the common network attack surface of a fully meshed network whose maximum is the total number of devices in the network. In addition, traffic traversing WhiteStar SNP does not need to stop or be stored within the cloud or on premises. This allows for high performance cloud-to-cloud or premises-to- premise communication without exposing any data to a third-party provider.
Encryption, Advanced Cryptography and Quantum Resistance
WhiteStar SNP utilizes NIST approved encryption algorithms implemented with patented cryptographic protocols. This allows WhiteStar SNP to roll encryption keys on every packet and be able to deploy changes to the encryption used across an enterprise instantaneously. WhiteStar SNP provides the industry’s first network technology that is both AI-enabled and Quantum-resistant. WhiteStar SNP eliminates cyberthreats today and is post-quantum- ready for when NIST approved quantum-resistant standard algorithms are required in the future.
Zero Trust (ZTNA) and Secure Identity
WhiteStar SNP is a next-generation, true zero-trust networking architecture that does not rely on any third-party authentication. Once user identity is verified, it is cryptographically secured with that user and that user’s devices thereafter by the WhiteStar SNP. WhiteStar SNP moves into the network layer functionality which previously had to be managed in each separate application, such as security, user identity, end point management, and much more.
The WhiteStar SNP
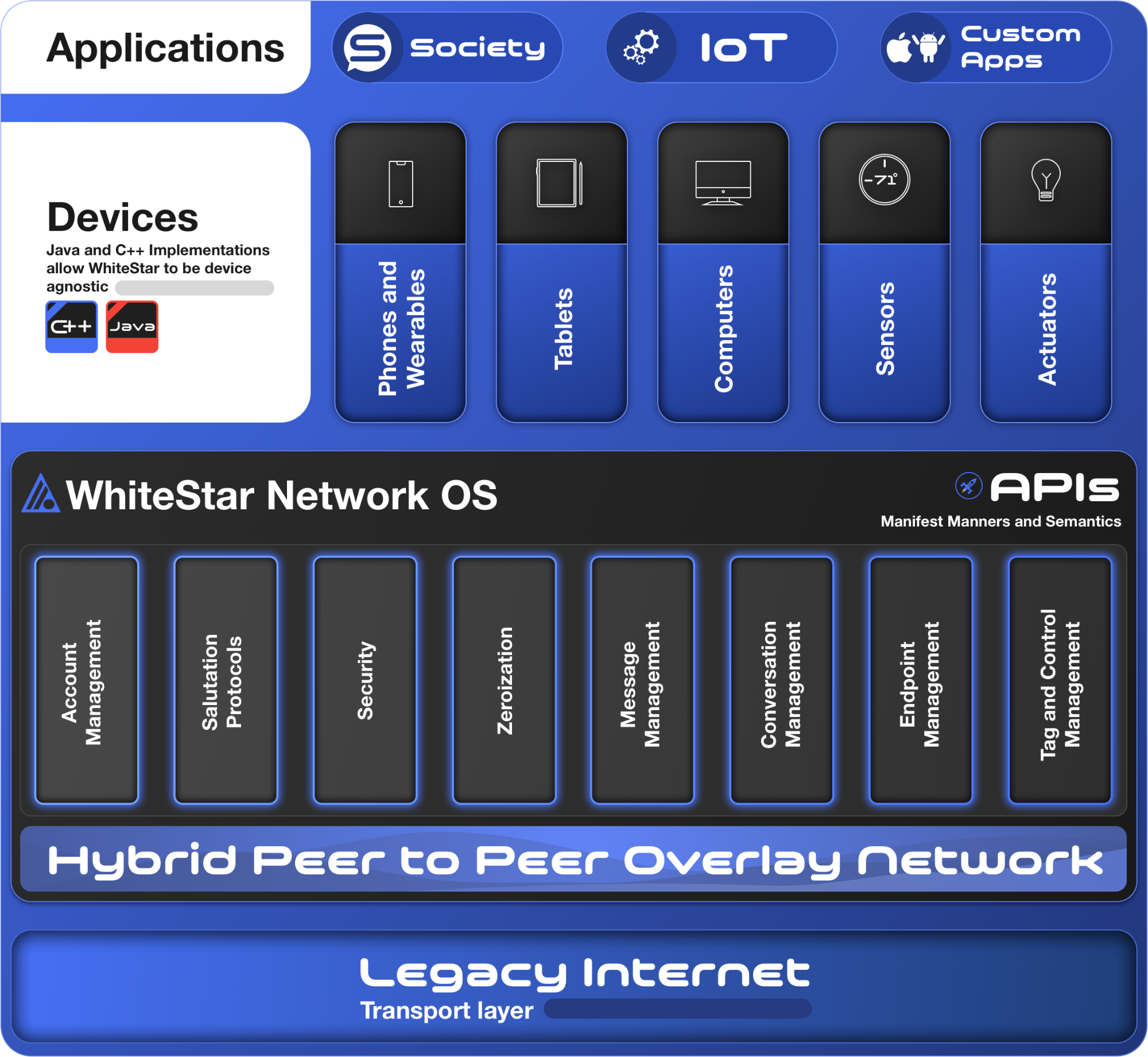
The WhiteStar SNP is a machine and device agnostic communications solution, capable of running on any modern smartphone or IoT device, and leverages the beyond-Moore’s-Law increase in compute and storage that has revolutionized the mobile and IoT industries in recent years. By using these billions of user devices to support the network, WhiteStar is capable of delivering a communications infrastructure built on a decentralized ecosystem.
Strong cryptography underpins the entire network, preventing hacking of user data and protecting user’s right of content ownership. Unlike with a Blockchain network, there are no tokens required to send messages or deploy projects on the WhiteStar SNP - instead, WhiteStar is available to create new applications in either of two form factors. The first is called StarFury and is designed to act as a bridge/adapter for data centers that need to integrate using micro services and REST APIs. The second is in the form of dedicated applications that have been integrated directly with WhiteStar’s APIs.
WhiteStar SNP is a fully featured solution for the next generation of network infrastructure, capable of being deployed with top-tier cryptographic security as an overlay to quickly and easily adapt existing and integrate new infrastructure, devices and machines into the network. WhiteStar makes deploying world-class security a snap, with no need for developers to have extensive training on complex security models and networking infrastructure, and it does so at a massively reduced cost over existing legacy Cloud-based and Blockchain networks.
WhiteStar’s Fundamental Shift to Enable Developer Success
The WhiteStar SNP fundamentally shifts the burden of networking, scaling, connectivity, transport, identity management and security into the networking layer from the application. This eases pain-points felt by all developers deploying applications on legacy Cloud based and Web3 systems, and addresses potential human error where a developer may not be a subject matter expert in any one particular area. This frees up vital human resources to concentrate on the application layer, saving valuable time and introducing an efficiency unavailable on other platforms.
For example, one powerful benefit of the inherent features of the WhiteStar SNP center around identity management. The current state of the art requires developers who want to manage user’s identities - and any personal identifiable information associated with their identities - in very particular ways to protect user privacy. However, given the inherent complexity and difficulty in device and application layer identity management, databasing and storage of PID, many developers who lack the skill, time, or are unwilling to properly manage user data leave vulnerabilities open in their applications. Likewise, centralized repositories of private user information, for example information stored in the Cloud, are juicy targets for would-be hackers seeking to compromise users’ privacy and steal personal information. This has serious implications when the targets hold immutable personal information like social security numbers, government identification, biometric data, among others, let alone information that could be financially damaging like bank account information, passwords, credit and debit numbers or private keys for cryptocurrencies.
However, by moving the burden of securing this kind of information out of the application and into the network, it efficiently eases the developmental overhead associated with properly securing private user data. WhiteStar is capable of intelligently securing user data at the end-device level, assured via a deceptively simple series of network semantics, artificial intelligence and cryptography that ensure user data is stored not only within the standards for best practice in user privacy protection, but also adapts to potential security threats as they emerge. Likewise, WhiteStar’s advanced feature set is fully capable of alerting users and developers to any potential security threats, to allow them to adapt to the changing environment and mitigate network risk before it becomes a problem. Once a “Bad Actor” is identified, the WhiteStar SNP also ensures that actor can no longer interact with users’ applications, further fortifying the Network and its attendant applications against external hostile action.
Because the burden of security is shifted to the Network, all of these benefits are baked in to any application deployed on WhiteStar, allowing developers to concentrate on building great applications without having to worry about securing the network back end. This illustrates the power of a properly architected platform that can appropriately underpin the next generation of application development.